Supervisory Control and Data Acquisition (SCADA)
SCADA generally refers to an industrial control system - a computer system monitoring and controlling a process. The processes can be industrial (e.g. manufacturing or power generation), infrastructure (e.g. water and sewage treatment, or electrical power transmission and distribution), or facility (e.g. environmental control in a building or on a ship). A SCADA system usually includes the following sub-systems:
- Human-Machine Interface (HMI) - the interface between the process control hardware and a human operator, via which the operator monitors and controls the process.
- A supervisory system - usually a computerised system that acquires process data and issues control commands to the process.
- Remote terminal units (RTUs) - these are units that receive analogue inputs from equipment and process sensors, convert the analogue data to digital data, and send the resulting digital data to the supervisory system.
- Programmable Logic Controllers (PLCs) - economical, versatile and easily configurable field control devices.
- A communications infrastructure - this is the element that connects the supervisory system with remote terminal units and field control units such as PLCs.
The term SCADA is usually used to describe systems in which the monitoring and control of a large industrial campus is centralised. Most control functions are performed automatically by RTUs or PLCs, with central control functions being restricted to supervisory level intervention. A PLC may control the flow of coolant for an industrial process, for example, but an operator may be able to override flow controls or initiate emergency action.
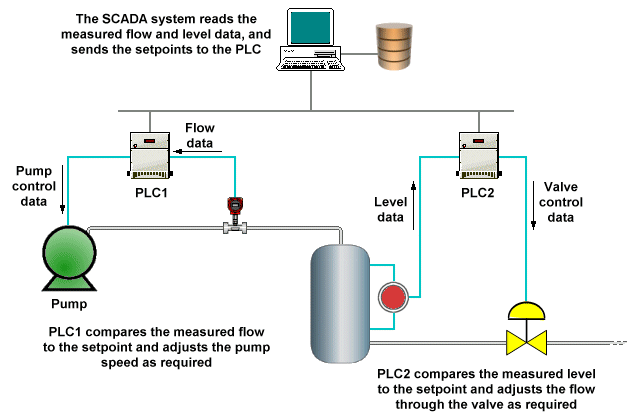
A typical SCADA system
Data acquisition starts with the RTU or PLC, and includes sensor readings and equipment status data that are transmitted to the SCADA supervisory system. The data thus acquired is put into human-readable format so that an operator can use it to make a decision whether or not to intervene or adjust control parameters. In the longer term, historical data can be collected and used for auditing and process performance analysis.
SCADA systems typically implement a distributed database that stores the input and output data recorded by the system (or calculated values derived indirectly from them). Each value is recorded in the database together with a time-stamp indicating precisely when the data was recorded (or derived), and the ID of the device or controller from which it was received. The system's HMI is usually linked to the database via diagnostic software that provides the operator with both real-time and historical graphical information about a process, as well as management information that can include device and system schematics, maintenance schedules, and troubleshooting guides. The system will also be able to trigger an alarm when normal operational parameters have been exceeded to allow an operator to take appropriate action.
SCADA was developed before computer networks as such existed, and the first generation of SCADA systems were never interconnected with other systems. Communication protocols were proprietary, and designed to be compact. In most cases an RTU only sent information when polled by the master station. Typical legacy protocols, which are all vendor-specific but widely-used, include Modbus RTU and Profibus. Standard protocols recognised by all major SCADA vendors include IEC 60870-5-101 or 104, IEC 61850 and DNP3. Many of these protocols now contain extensions to allow them to operate over TCP/IP. With the advent of the local area network, processing could be distributed across multiple stations, which shared information in real time, although the networking protocols used were still mostly proprietary. The current generation of SCADA systems use open protocols and standards, allowing functionality to be distributed across a WAN using Internet protocols, and facilitating interoperability with peripheral devices such as printers. The ability to interconnect SCADA systems with other networks via the Internet has, inevitably, raised concerns about security.
SCADA systems are now based on standard network technologies. Ethernet and TCP/IP based communications protocols are replacing the older proprietary ones. Next-generation SCADA protocols look set to adopt web technologies, allowing them to be accessed via a wide range of end-user devices, including mobile and hand held devices. Some vendors have even begun to offer application-specific SCADA services hosted on Internet servers, eliminating the need to install systems at the end-user’s premises, although there are again some concerns about security, latency, and the reliability of Internet connections. The security of SCADA systems connected to public networks, or to other systems via public networks, is an important issue, since any breach of security could have serious consequences. Vulnerabilities in a power distribution system, for example, could result in widespread power failures that could involve businesses in financial losses or have serious consequences for safety. Vendors of SCADA systems have now begun to address these risks for TCP/IP-based SCADA networks.
